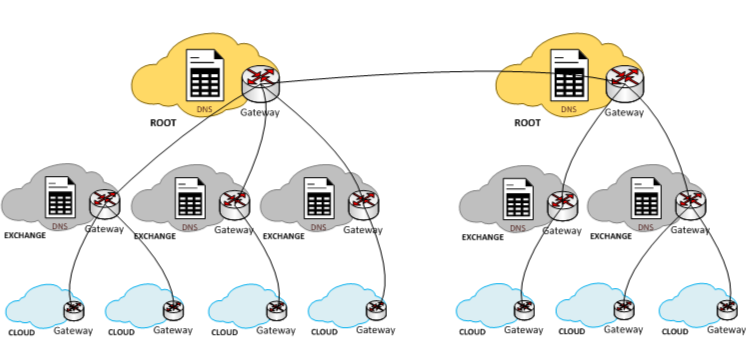
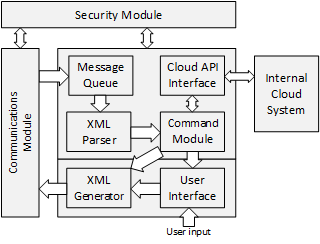
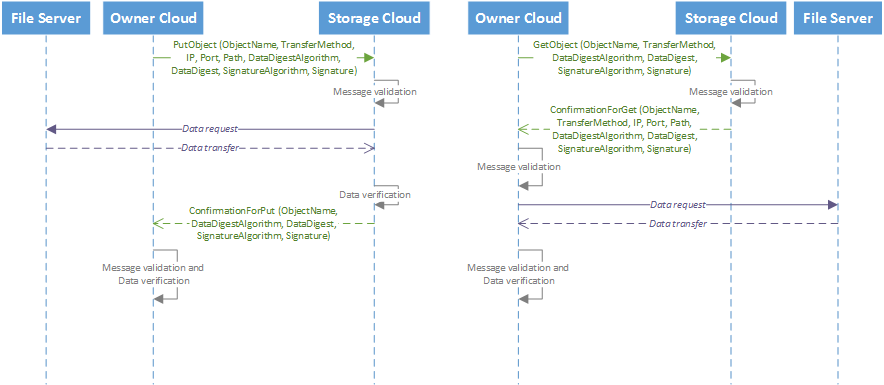
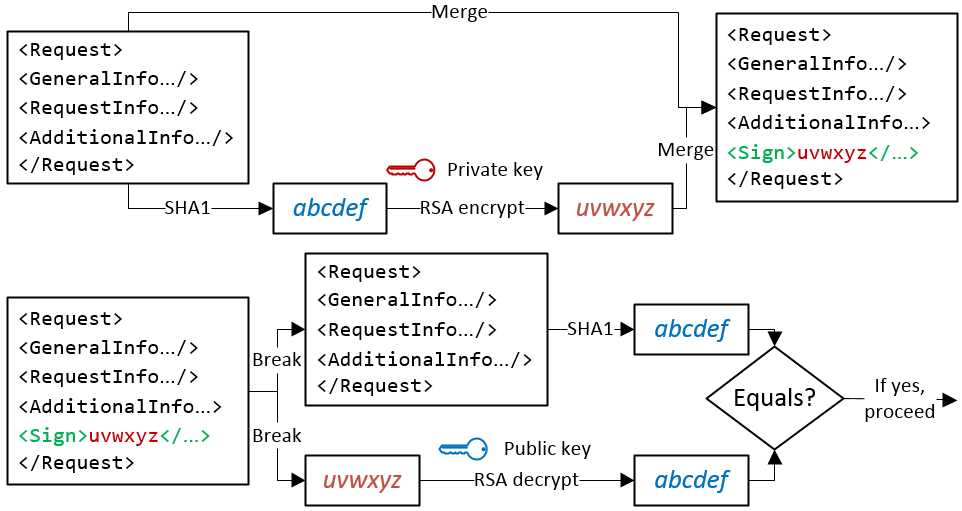
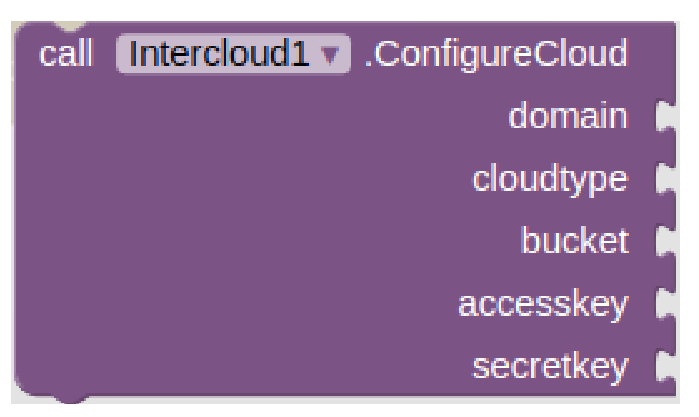
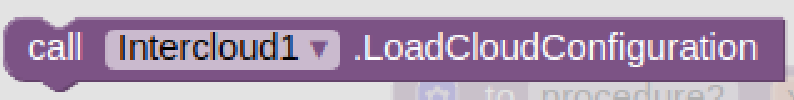
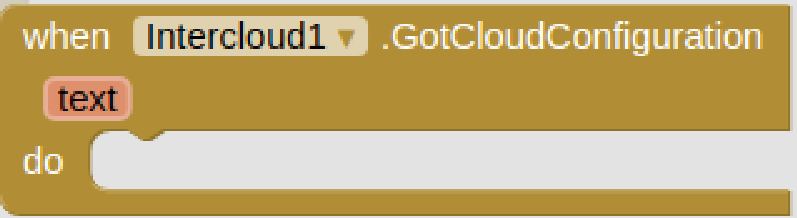
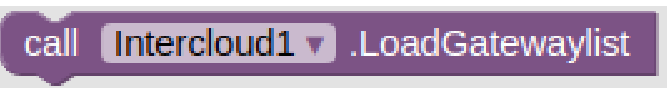
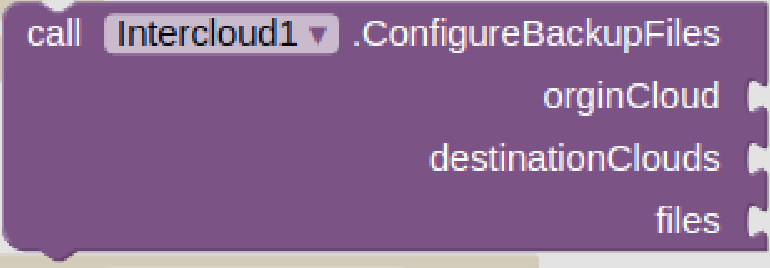
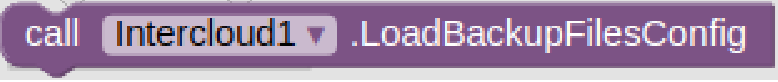
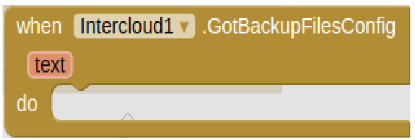
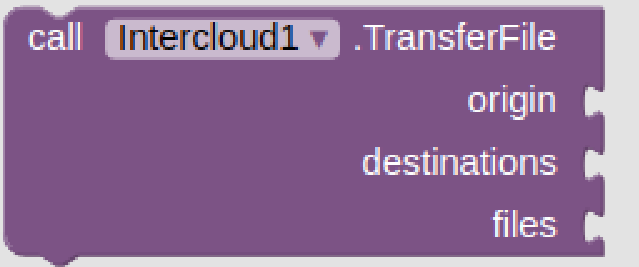
Inspired by the successful HyperText Transfer
Protocol (HTTP), an extensible protocol called the Intercloud Communications
Protocol (ICCP), was created. ICCP allow clouds to communicate with
each other securely using the same protocol, which is transparent
to the underlying APIs of different clouds. Since the ICCP is based
on the Extensible Markup Language (XML), it greatly facilitates
the development of Intercloud applications. It also includes security
functions or measures to ensure confidentiality and integrity depending
on different cases.
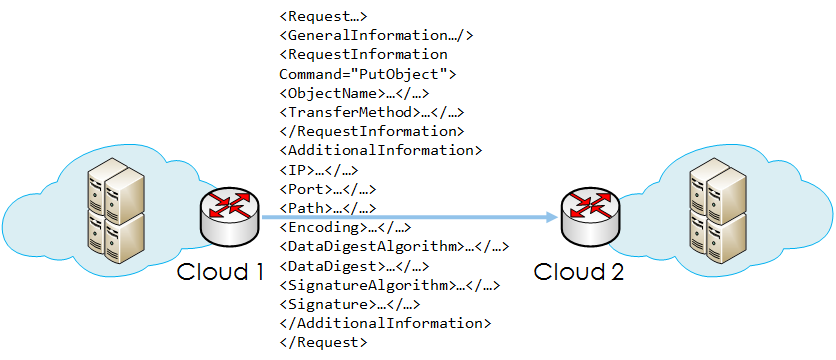
In summary, clouds communicate with each
other by exchanging XML-based messages, of which there are three
types: Request, Response, and Exception with two major attributes,
Version and ID. “Version” specifies the version number of the protocol
while “ID” identifies the request-and-response or request-and-exception
pair (i.e., for session identification purposes). Within a message,
General Information, Request/Response/Exception Information, and
Additional Information can be defined in the “GeneralInformation,”
“RequestInformation,” “ResponseInformation,” “ExceptionInformation,”
and “AdditionalInformation” tags, respectively. In general, the
messages can be described using XML schemas here.
General Information provides the general
information of the message. In the “GeneralInformation” tag, the
sending cloud is specified in the “From” attribute, while the receiving
cloud is specified in the “To” attribute. The “Date” and “Time”
define the date and time of the creation of the message, respectively.
Request/Response/Exception Information provides request/response/exception-specific
information. The Command attribute provides the command for the
request (i.e., similar to the action used in HTTP). Additional Information
provides the additional information to be included in each message
(e.g., data). Based on the aforementioned schemas, different tags
can also be defined. They are similar to HTTP headers in providing
specific information or functions.